Visualize Change with an Out-of-the-Box Configuration Report
By: Mia LaVada, Product Manager of CIS Benchmarks and Cloud
Your technology is always changing, and you often end up playing catchup to secure it. This is difficult in the cloud when you share security responsibility with the cloud service providers (CSP). You need to know what’s changing so that you can best ensure security in the cloud.
Brush up on your duties under the shared responsibility model.
I understand that this need to know what’s changing extends to CIS Hardened Images. When we update these pre-hardened virtual machine images (VMIs) once a month to apply updates issued by the vendor, you may be left wondering what changed from last month’s version to this month’s version.
We hear you. That’s why the Center for Internet Security (CIS) is releasing an out-of-the-box configuration report. Its purpose is to give you visibility into the software updates we implement from one month to the next and into the base operating system's compliance with the CIS Benchmark standard.
A Pre- and Post-Hardening View
Let’s begin with what you have currently. When you’re using a CIS Hardened Image, you get a CIS-CAT HTML report of the hardened system. This report will show a score for overall compliance with the associated CIS Benchmark.
With this feature enhancement, you can now view the compliance score for the base operating system (OS) and its associated packages prior to CIS hardening it. This provides a couple of benefits:
- You can use the out-of-the-box configuration report to understand what’s changed in the hardening process and how the Hardened Image will improve the security of your OS.
- You can drill down into the out-of-the-box configuration report to see the configuration of the base operating system without modification from CIS.
Let's use a CIS-CAT Pro scan against CIS Microsoft Windows Server 2022 Benchmark Level 1 v1.0.0 to demonstrate. Here's a look at what an out-of-the-box configuration report might look like, which can vary based on the cloud platform.
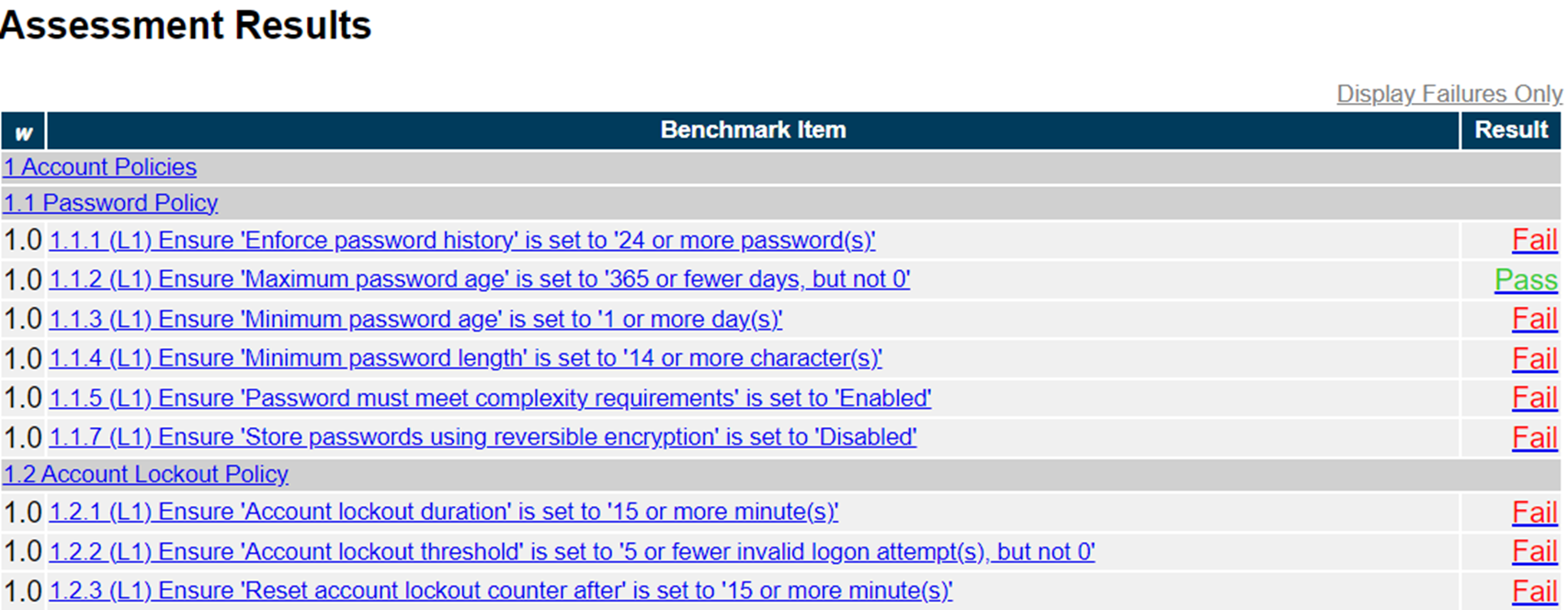
And here's the post-hardening view. Notice how all the Benchmark items in view have switched from "Fail" to "Pass."
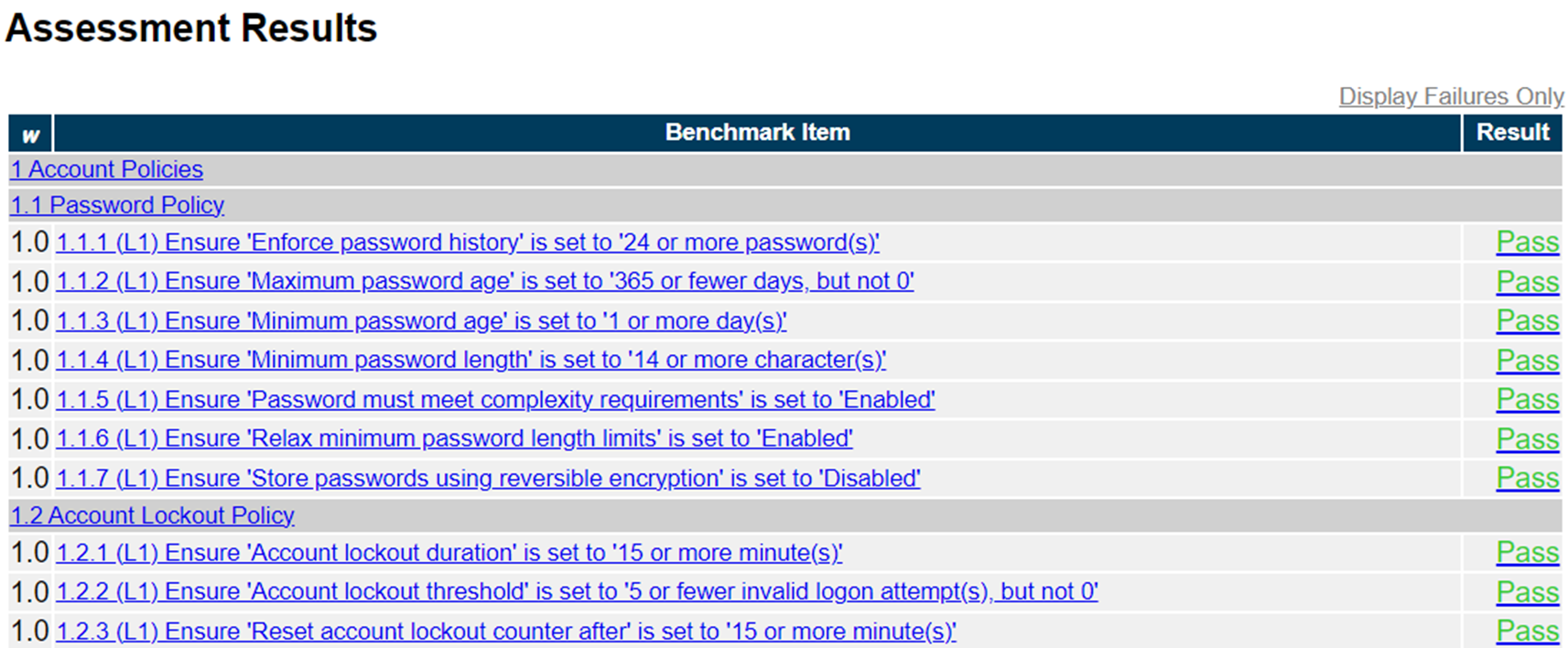
Sometimes, a few minor exceptions within the CIS Hardened Images deviate from the CIS Benchmarks guidance. When that happens, we list those settings in the Exceptions file within the Hardened Image. You can also use this file to help keep track of any changes that have occurred between different versions of a CIS Hardened Image.
Here's where you can find these reports and files:
- For Windows products, both reports along with the Exceptions file live in the C drive in a folder titled "CIS_Hardening_Reports." The CIS-CAT report is labeled "CIS-CAT_Report.html," and the Exceptions file is labeled "Exceptions.txt."
- In Linux products, the content is available in the home folder (same folder title) "CIS_Hardening_Reports." Its files use the same two names as with Windows product. The CIS-CAT report is labeled "CIS-CAT_Report.html," and the Exceptions file is labeled "Exceptions.txt."
No More Playing Catch-up
We want to ensure your ability to easily identify the configurations of a CIS Hardened Image. We believe this new feature will enable that.
At this time, we are rolling out this functionality for AWS and Azure Linux Hardened Images. We will continue to roll out implementation on the other platforms and technologies with a completion goal of the second quarter of 2023. In the meantime, we look forward to hearing what you think about this feature enhancement so that we can make it even better going forward.
About the Author

Mia LaVada is a product manager for the CIS Benchmarks and Cloud products at the Center for Internet Security (CIS). She has been with CIS since June 2019. As a strong believer in the power of community, Mia regularly works with CIS Members to help ensure CIS addresses the needs of the global cybersecurity community. She’s also particularly passionate about finding solutions to further secure the ever-changing cloud ecosystem.